Massive Machine Type Communication
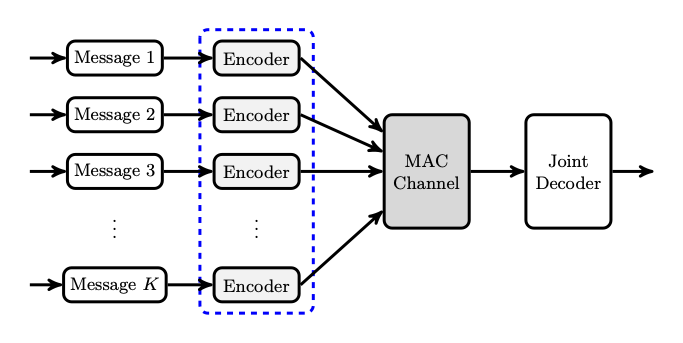
Machine-type communication (MTC) is predicted to surge in the near future, disrupting the foundation on which most wireless systems are built. This envisioned growth poses new challenges for existing communication infrastructures designed with human connectivity in mind. This transition to MTC data transfers has been recognized by several researchers in recent years, yielding several important contributions along this direction. More specifically, the emergence of myriad unattended devices, each with a singular or narrow purpose, jeopardizes connection-based wireless infrastructures. The combination of a very large device population together with unorthodox traffic characteristics can be viewed as the culprit of this precarious situation. Most unattended devices are predicted to only transmit information sporadically and evidence suggests that messages generated by many machines will be brief, fitting within one short payload. These traffic attributes break the acquisition-estimation-scheduling paradigm as an efficient means to enable wireless Internet access. The conventional design of wireless systems for human-operated devices has been informed by a few auspicious attributes. The density of human-operated devices is bound to stay on the same order as the population within an area. This allows the real-time acquisition of device identities and the continual cataloging of their presence within the reach of an access point. Moreover, humans typically give rise to sustained connections with their data transfers lasting several scheduling cycles. As such, the physical resources dedicated to acquisition, the estimation of individual channels, and the procurement of buffer states can be amortized over the duration of a typical connection. This situation underlies the great success of opportunistic scheduling as a means to efficiently manage spectral resources in wireless environments. It may be worth noting that, in many past academic contributions on wireless scheduling, the cost of maintaining state information regarding channels and queues is not accounted for while assessing the performance of the ensuing systems. Rather, these resource expenditures are implicitly discounted over the lengths of sustained connections, or they are dismissed as inconsequential compared to the energy and spectrum devoted to the explicit transfer of information. However, when device density skyrockets and data transfers become sporadic and ephemeral, gathering information and disseminating schedules via feedback becomes cost prohibitive.
The realization by the research community that resource allocation through individualized feedback can only offer partial answers to the challenges of tomorrow is evinced by a recent propensity by scholars to look for alternate paradigms. The revival of random access for wireless systems exemplifies the need to address the sporadic and uncoordinated nature of machine-driven communications. This departure from established solutions also points at the difficulty of facilitating the transmission of short payloads, as opposed to sustained connections. Small packets akin to those generated by sensors and IoT devices lead to transient data transfers. This precludes the type of amortization described above whereby spectral resources are spent with the goal of maintaining long connections. Another prime aspect of emerging wireless traffic pertains to resolving the identities of active devices. When the number of devices within an area becomes very large, with only a subset of them being active at any point in time, the problem of allocating resources (e.g., codebooks, subcarriers, signature sequences) to every user in order to manage interference becomes excessively complex. Since devices are unaware of who else is in the active set, they cannot apportion resources to themselves in a distributed fashion. Here again, a more centralized solution with detailed feedback is impractical. This forces active users to act in an uncoordinated fashion or, from an information theoretic perspective, to use identical codebooks. This constraint substantially complicates the design of computationally-efficient decoding algorithms that offer good performance. When the number of devices within a cell is huge and the set of active devices changes rapidly, the task of repetitively resolving identities through decoding becomes insurmountable. Despite this reality, several IoT access schemes found in the literature assume that each device uses its own prescribed codebook. Implicitly, this is equivalent to the access point being aware of who is transmitting, with every device being assigned a specific encoder. Consequently, established sourced paradigms for wireless access are inadequate for MTC traffic; prior work on random and multiple access is vast, inspirational, yet inapplicable without substantial modifications to the problem at hand. As we will see, this challenge can be addressed by leveraging the inherent sparsity in the low activity factor within a large IoT device population.